Network connection describes the extensive process of connecting various parts of a network to one another through the use of Components like Routers, Switches, Gateway and Protocols etc.
MTR
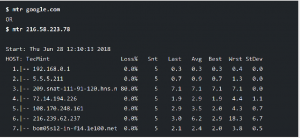
MTR is a simple, cross-platform command-line network diagnostic tool that combines the functionality of commonly used traceroute and ping programs into a single tool. In a similar fashion as traceroute, mtr prints information about the route that packets take from the host on which mtr is run to a user specified destination host.Once you run mtr, it probes the network connection between the local system and a remote host that you have specified. It first establishes the address of each network hop (bridges, routers and gateways etc.) between the hosts, it then pings (sends a sequence ICMP ECHO requests to) each one to determine the quality of the link to each machine.
The simplest example of using mtr is to provide the domain name or IP address of the remote machine as an argument, for example google.com or 216.58.223.78. This command will show you a traceroute report updated in real-time, until you exit the program (by pressing q or Ctrl + C).
Ping
Ping is a network utility used to see if the end user can reach other devices connected to the internet. When using Ping, always test a few different sites to see if it is just one site or all sites.
To ping a device, proceed as follows.
1.Open a Windows/Linux Command Prompt window.
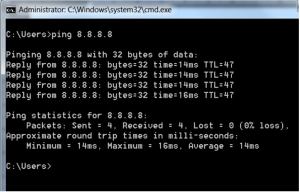
2.At the command prompt, type, ping <IP address>, as shown below.
You can interrupt Ping at any time by holding down the CTRL key, and pressing C on your keyboard. Ping operates by sending ICMP Echo Request packets to the target device and waiting for an ICMP Echo Reply. The program reports errors, packet loss, and a statistical summary of the results.
Netstat
netstat is a command-line network tool that is a handy troubleshooting command. Its cross-platform utility means you can use it on Linux, macOS, or Windows.
netstat can be very handy in the following.
1.Display incoming and outgoing network connections
2.Display routing tables
3.Display number of network interfaces
4.Display network protocol statistics
To start with netstat, let’s see the command that displays all connections.
netstat -a
Type the above command and hit enter. You will see all the active connections from different states as shown below.
More example of netstat:
https://www.tecmint.com/20-netstat-commands-for-linux-network-management/
Tcptrack
tcptrack displays the status of TCP connections that it sees on a given network interface. tcptrack monitors their state and displays information such as state, source/destination addresses and bandwidth usage in a sorted, updated list very much like the top command.
tcptrack requires only one parameter to run: the -i flag followed by an interface name that you want tcptrack to monitor. This is the most basic way to run tcptrack:
# tcptrack -i eth0
tcptrack can also take a pcap filter expression as an argument. The format of this filter expression is the same as that of tcpdump(8) and other libpcap-based sniffers. The following example will only show connections from host 10.45.165.2:
# tcptrack -i eth0 src or dst 10.45.165.2
The next example will only show web traffic (ie, traffic on port 80):
# tcptrack -i eth0 port 80
Firewall
Network firewalls filter your traffic for excessive amounts entering your network. This can protect from bot and denial of service attacks. When these packets are detected, you’ll be able to report specific attack vectors to your management console via the logging capability of your firewall.
One of the main firewall using in Linux environment is CSF. Config Server Firewall (or CSF) is a free and advanced firewall for most Linux distributions and Linux based VPS. In addition to the basic functionality of a firewall – filtering packets – CSF includes other security features, such as login/intrusion/flood detections. CSF includes UI integration for cPanel, DirectAdmin and Webmin, but this tutorial only covers the command line usage. CSF is able to recognize many attacks, such as port scans, SYN floods, and login brute force attacks on many services. It is configured to temporarily block clients who are detected to be attacking the cloud server.
Windows Firewall is a stateful host firewall that drops all unsolicited incoming traffic. This behavior of Windows Firewall provides some protection from malicious users and programs that use unsolicited incoming traffic to attack computers.